Atomic access control
Published: Fri 15 November 2019
At Peergos we care deeply about your privacy, and the core of privacy is access control. Controlling who can see what. We've made some big improvements in this area for our new v0.1.4 release, so let's learn some more about them.
We have totally rewritten our access revocation implementation. Previously there were some issues with nested write access which could cause data loss. Now in the new version, revoking write access is a single pass over the files and directories you are revoking access to, rather than 3. We've also made it atomic. This means your machine can crash at any point and your file system is in a consistent state with all data present.
Similar improvements have been made to revoking read access and we are working on fuzzing the access control mechanism to further assure correctness and safety. While we had the hood popped open, we also removed unnecessary reloads of the current directory which has made the web interface much snappier.
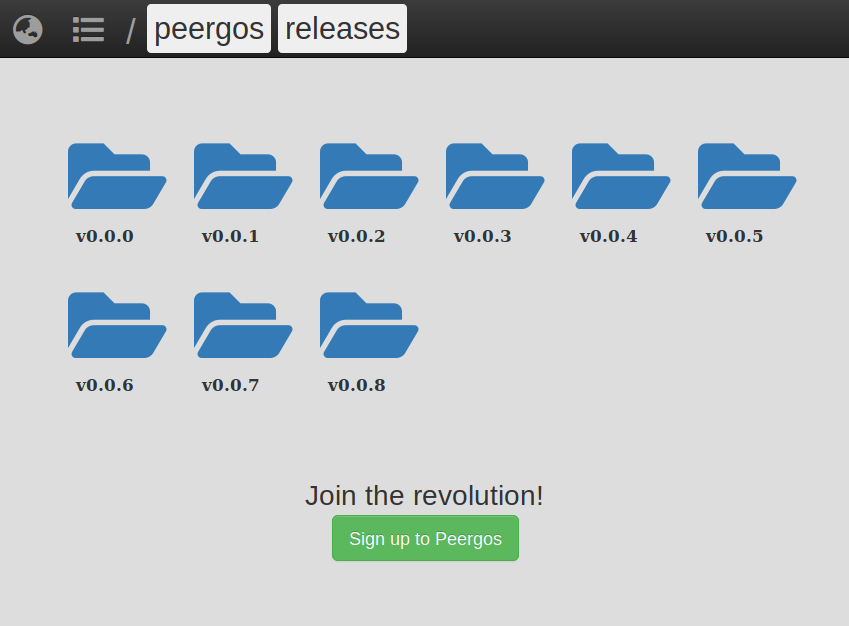
New public link UI for https://peergos.net/public/peergos/releases
We also have a secret to share with you - we have a mechanism for making files public, though it is not added to the web interface yet. Each user can choose to publish a capability to a file or folder that is readable to anyone. The mechanism for this is each user publishing a merkle CHAMP root, which is a lookup from path to capability. This is currently only used by the "peergos" user for releases of Peergos itself: https://peergos.net/public/peergos/releases.

Old public link UI for https://peergos.net/public/peergos/releases
Prior to this release, public files were decrypted server side after retrieving the capability from this CHAMP and delivered directly to the requestor. Clearly if we allowed anyone to use the feature then it would be a trivial cross-site-scripting (XSS) vector. So, in preparation for allowing all users to publicly share files, we now make the server retrieve the capability, and then do a http redirect to a "secret link" to that file. This means we get the full Peergos interface for navigating, viewing and downloading public files, and removes the potential for XSS attacks. The file or directory then becomes accessible under the human readable url
https://peergos.net/public/$path-to-file
Want to be part of the future? Create an account on https://peergos.net or self-host your own private personal datastore.
RECENT POSTS
- 2025 - What a year!
- Decentralization Matters
- Security audit 2024
- Reasons to prefer blake3 over sha256
- A better web
- Markdown browser
- Release the BATs (block level access control in IPFS)
- Encrypted email storage and client
- Decentralized encrypted chat
- Peergos launches decentralized & encrypted social media
- Private and customizable profiles
- Simple decentralized web hosting on Peergos
- Encrypted shareable calendar
- Fast Encrypted File Search
- Private Planning Boards in Peergos
- How to solve the social dilemma and fix social media
- Peergos wins EU Next Generation Internet grant
- Direct S3 access
- Peergos release v0.3.0
- Keybase has left the building
- The perfect social network
- Atomic access control
- Peergos release v0.1.3
- Applications on Peergos
- Fast seeking and encrypted history
- IPFS Camp, new features
- Alpha Release
- Security Audit
- Development update